Approaches to Message Authentication
34 What properties must a hash function have to be useful for message. In all of these approaches an.

Message Authentication Requirements Geeksforgeeks
An Integrated Approach Abnormal Psychology Distributed Systems Approaches TO Message Authentication Approaches TO Message Authentication -.
. Message authentication is to protect the message integrity and to perform sender authentication. There are two approaches to message authentication. 32 What is a message authentication code.
Data encryption standard DES. A code is attached to each message by the sender and verified by the session partner. 31 List three approaches to message authentication.
The desired Message Authentication. 34 What properties must a hash. The three approaches to message authentication are i.
This is achieved through different mechanisms that are. 34 What properties must a hash function have to be useful for message. 31 List three approaches to message authentication.
As part of the. 2Use of TagsA tag is attached to the message at source using a. 32 What is a message authentication code.
Message Authentication without Message Encryption We examine several approaches to message authentication that do not rely on encryption. 1 Message Authentication Code MAC 2 Message Authentication 3 Secondary authentication We encourage you to add two methods for authentication to your account. 34 What properties must a hash function have to be useful for message.
31 List three approaches to message authentication. 1Use of ciphertext An encryption algorithm E is applied to a message M using a key K to produce an authenticated ciphertext. 31 List three approaches to message authentication32 What is a message authentication code34 What properties must a hash function have to be useful for message.
Approaches to message authentication. 34 What properties must a hash function have to be useful for message. The first approach uses public-key encryption which means the user must provide a public key a message that gives the user permission to.
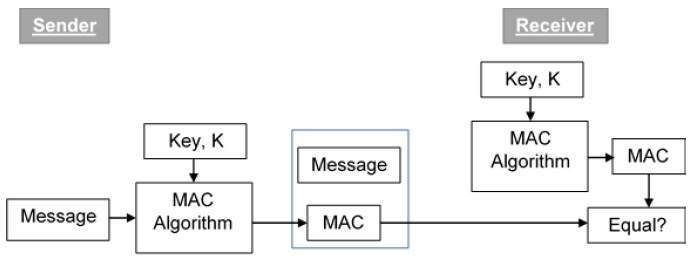
32 What is a message authentication code. Briefly describe the three ways illustrated in Figure 32 of message authentication using a one-way hash function. Answer a A hash code is computed from the source message encrypted.
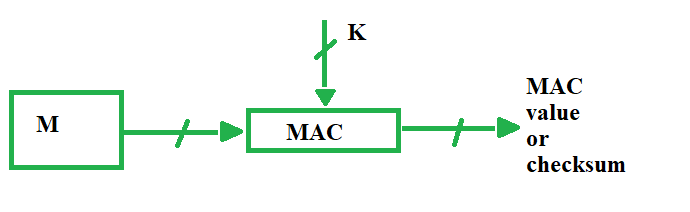
Three approaches to message authentication. 32 What is a message authentication code. This module describes message authentication code MAC which is based on symmetric.
The main use in SSH is with HMAC or hash-based message authentication codes. Message authentication is possible by simply performing symmetric encryption. Authentication with Conventional Encryption If we assume that only the sender and receiver share a key then.
There are two methods for producing the message authentication code. 31 List three approaches to message authentication. For establishing MAC process the sender and receiver share a symmetric key K.
MAC algorithm is a symmetric key cryptographic technique to provide message authentication. Approaches to message authentication Message authentication refers to ways in which message integrity is maintained. 32 What is a message authentication code.
31 List three approaches to message authentication. These are used to ensure that the received message text is intact and unmodified.

Message Authentication Requirements Geeksforgeeks
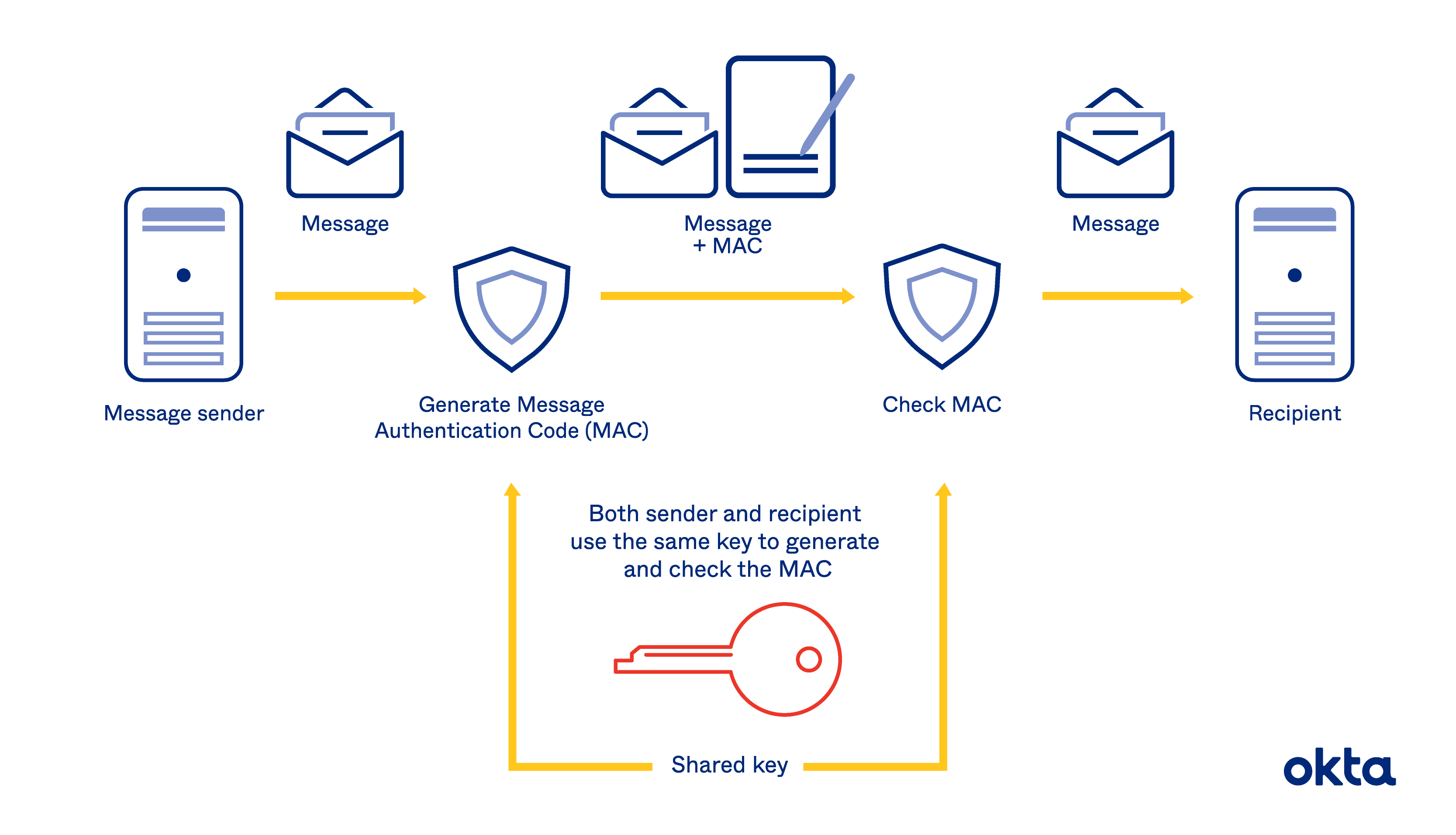
Hmac Hash Based Message Authentication Codes Definition Okta
No comments for "Approaches to Message Authentication"
Post a Comment